Auditing Euler Vault Kit (Euler V2) with Olympix AI VS Code Extension
Step-by-step guide to analyze the Euler Vault Kit codebase for security vulnerabilities using the Olympix Web3 Cybersecurity Assistant.
Auditing Solidity Contracts with Olympix AI
Olympix is Web3’s first enterprise-grade, proactive DevSecOps platform that transforms blockchain security from an afterthought into an integrated, continuous process. Rather than relying solely on external audits, Olympix empowers blockchain teams, DeFi protocols, and enterprises to proactively secure their smart contracts in-house from day one.
Built specifically for safeguarding high-value assets on-chain, Olympix uses AI to help developers:
- Detect vulnerabilities early.
- Reduce audit dependency.
- Build secure code as part of everyday workflows.
This tutorial shows how to leverage Olympix AI’s VS Code Extension to audit a real-world Solidity codebase, step-by-step.
What You'll Learn
- How to set up and configure Olympix AI’s VS Code Extension.
- How to audit Solidity codebases like Euler Vault Kit (Euler V2) for vulnerabilities.
- How Olympix uses AI to explain findings and suggest fixes.
1. Clone the Repository
First, clone the Euler Vault Kit and checkout the known-v2 commit:
2. Open VS Code Extensions Panel
- Open the Command Palette (
Cmd+Shift+P/Ctrl+Shift+P) - Run View: Show Extensions
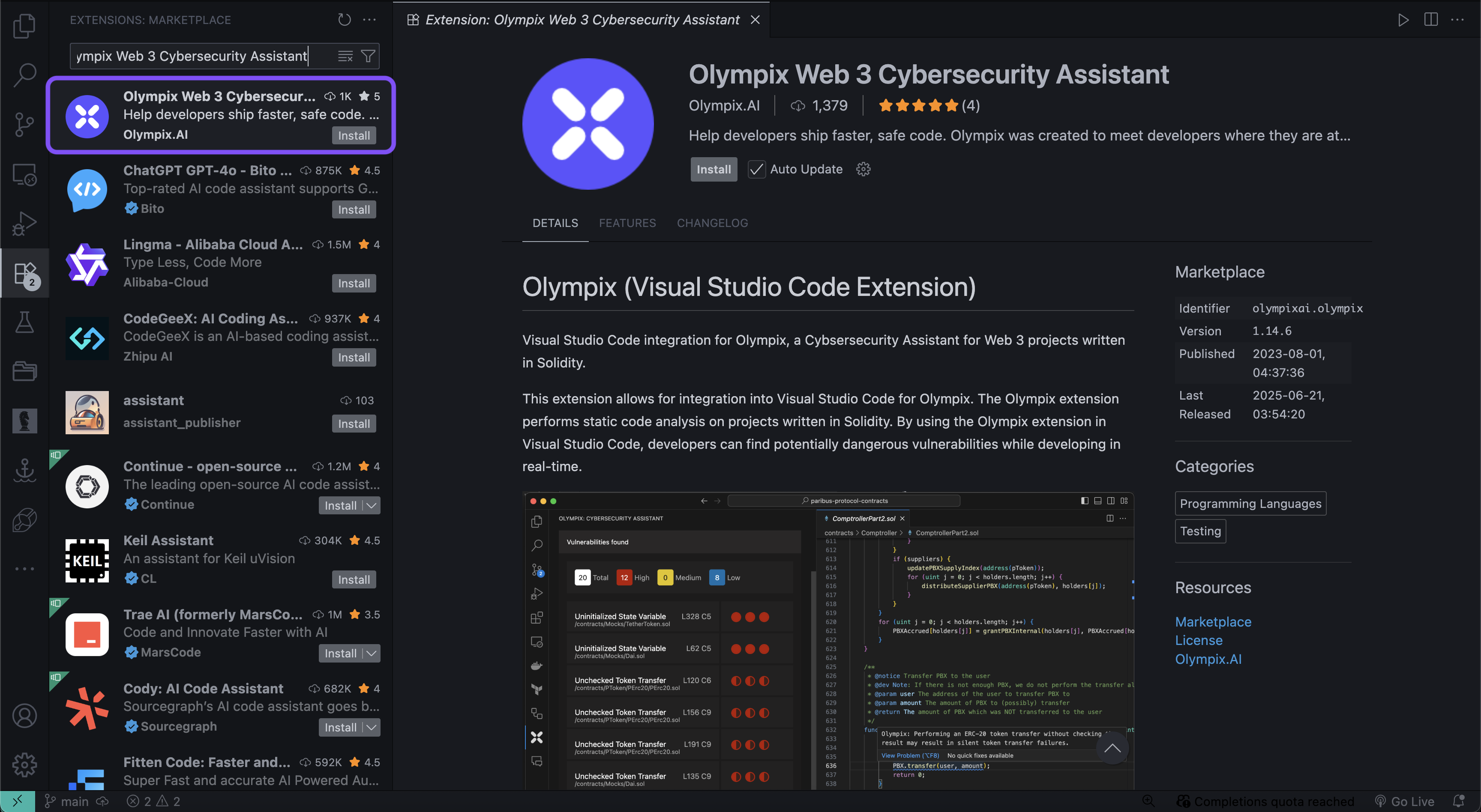
3. Install Olympix Extension
- In the Extensions search box, type “Olympix Web 3 Cybersecurity Assistant”
- Click Install
4. Authenticate Olympix
- Click the Olympix icon in the sidebar to the left
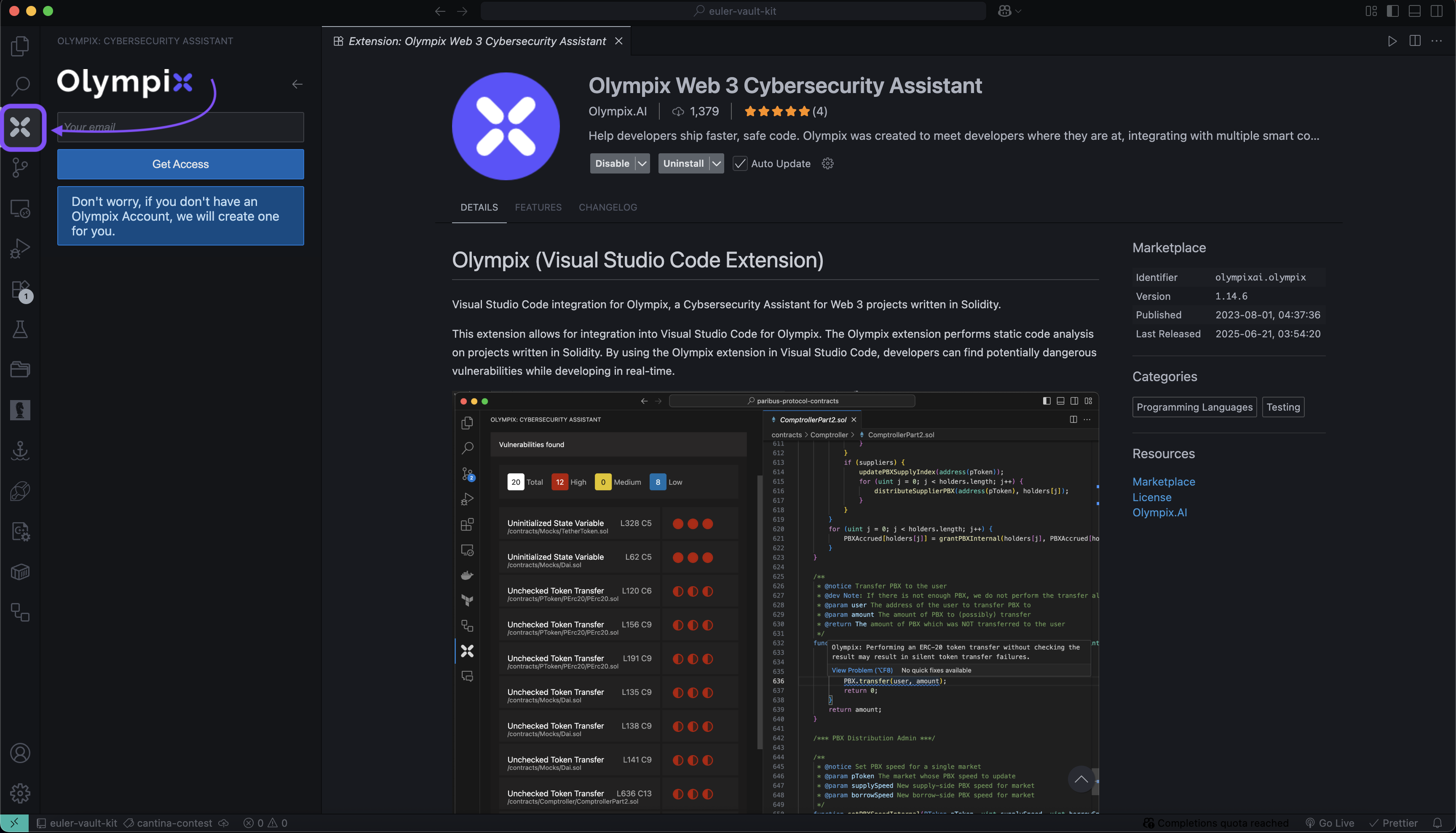
- Enter your email when prompted
- Check your inbox for the verification code
- Paste the code into the modal to unlock the extension
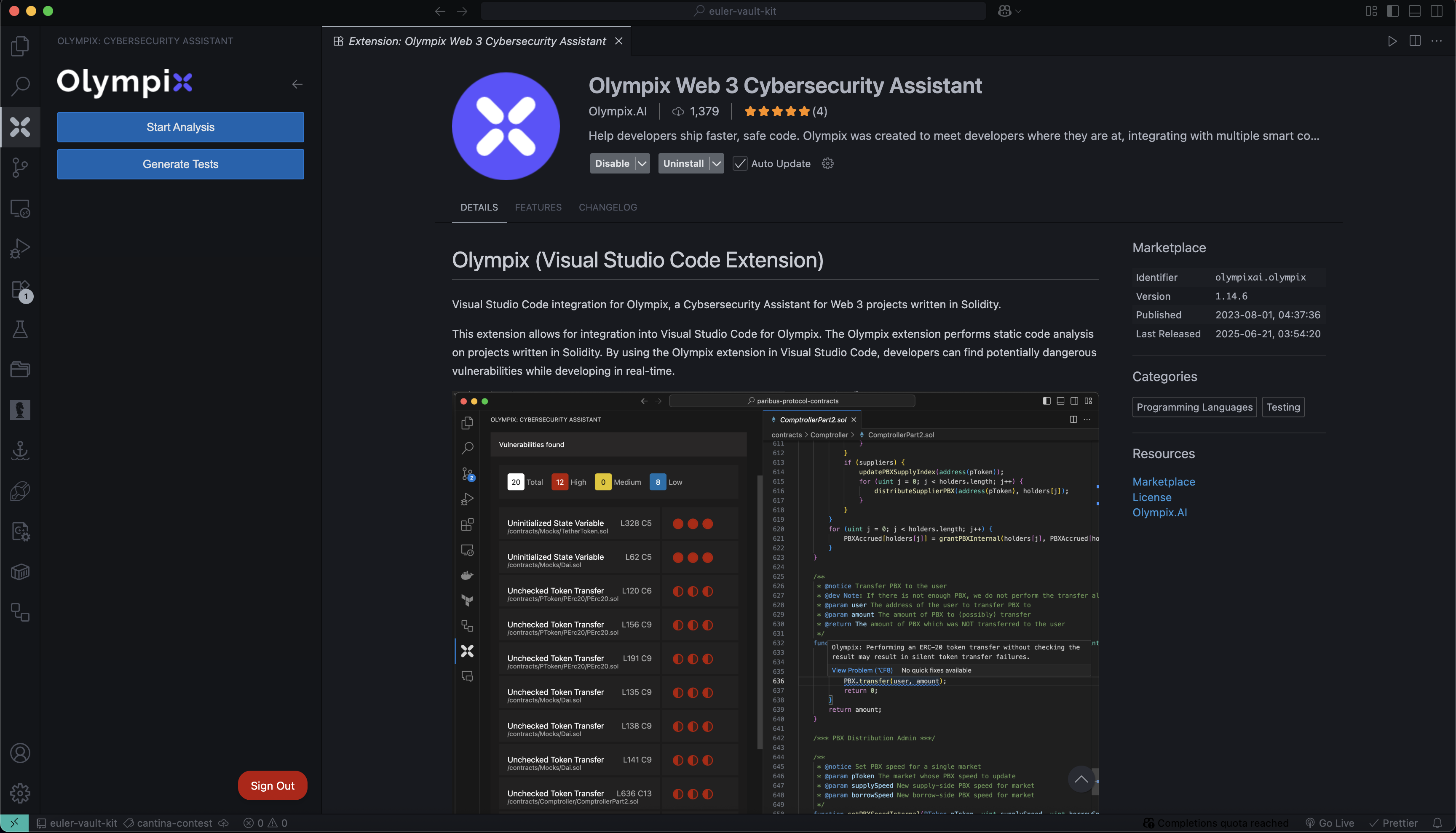
5. Run the Vulnerability Analysis
- Open the root folder of the project in VS Code
- Click the Start Analysis button in the Olympix pane
Note: The first run can take 3–5 minutes. If it hangs or fails, cancel and retry.
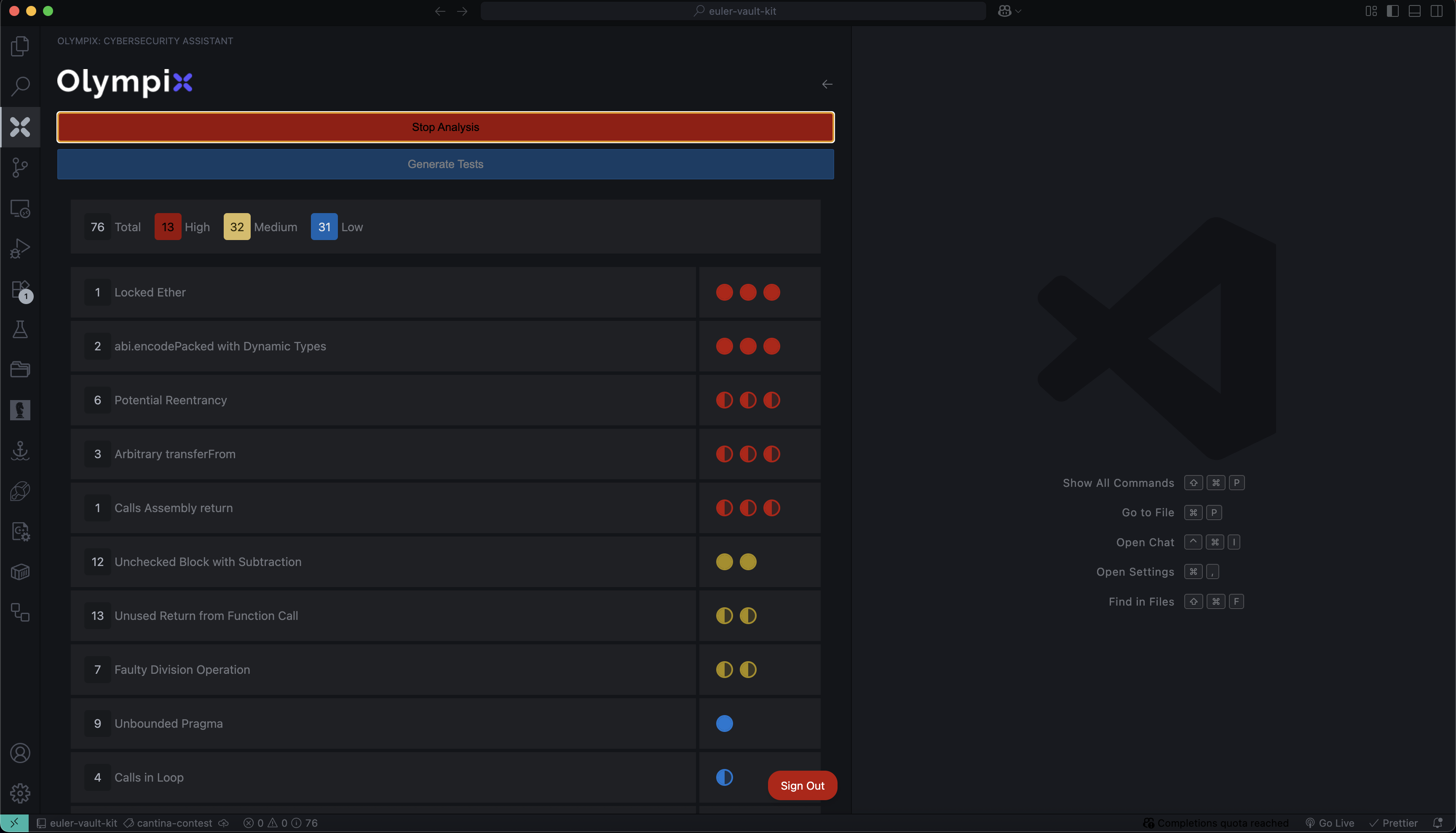
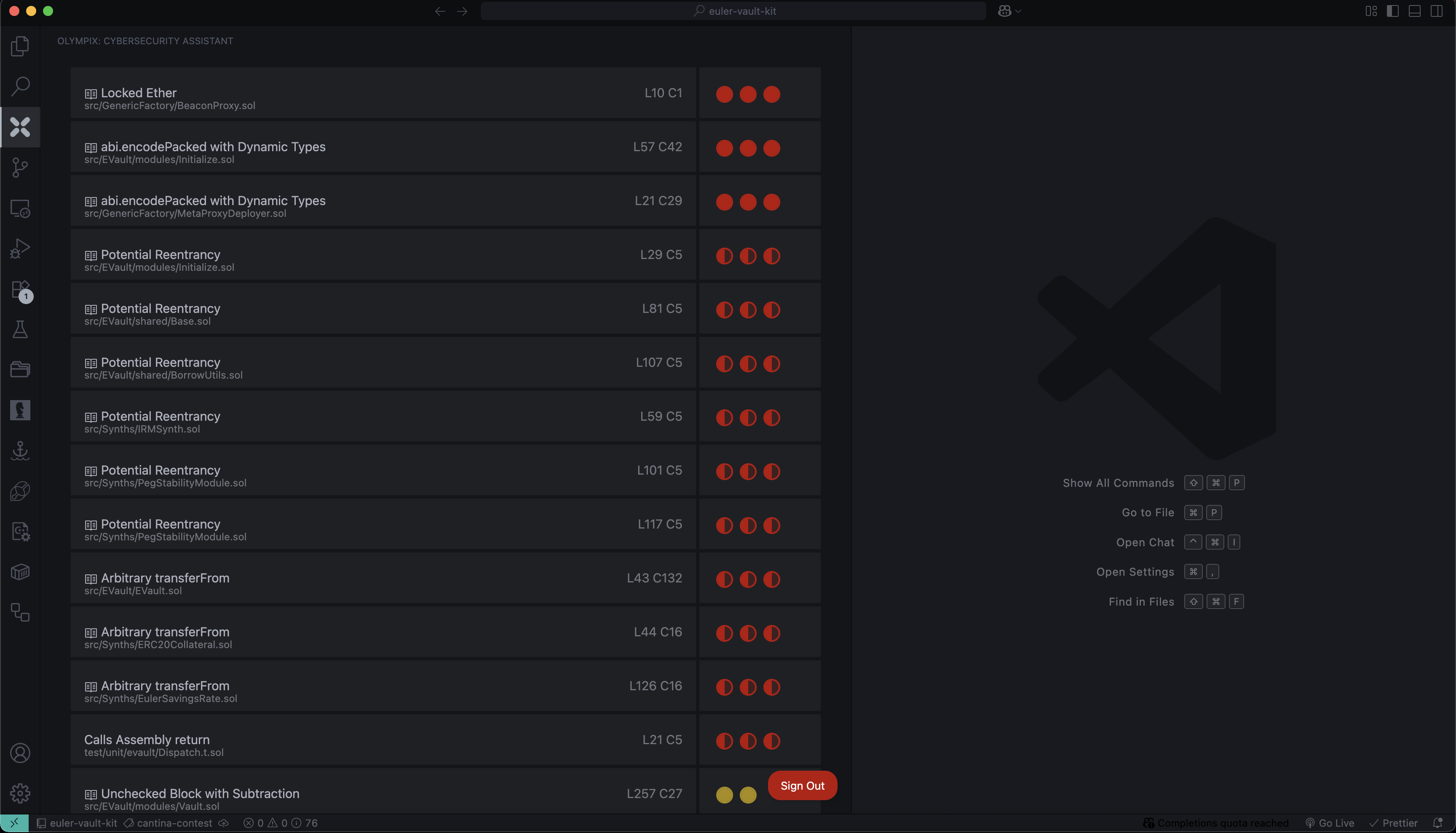
6. Review Findings
Once complete, Olympix will list:
- Vulnerabilities with severity & confidence
- File paths and line numbers
- AI-generated explanations
7. Deep Dive Example
Below are some vulnerabilities that Olympix AI flagged in the Euler Vault Kit (Euler V2).
Vulnerability 1: Locked Ether
What is the Locked Ether vulnerability?
When a contract accepts ETH but provides no way to withdraw it, those funds become permanently “locked” in the contract’s balance.
Real-world example:
In 2017, a bug in Parity’s multisig wallet library allowed an attacker to self-destruct the shared library contract, freezing over 513 000 ETH across thousands of wallets.
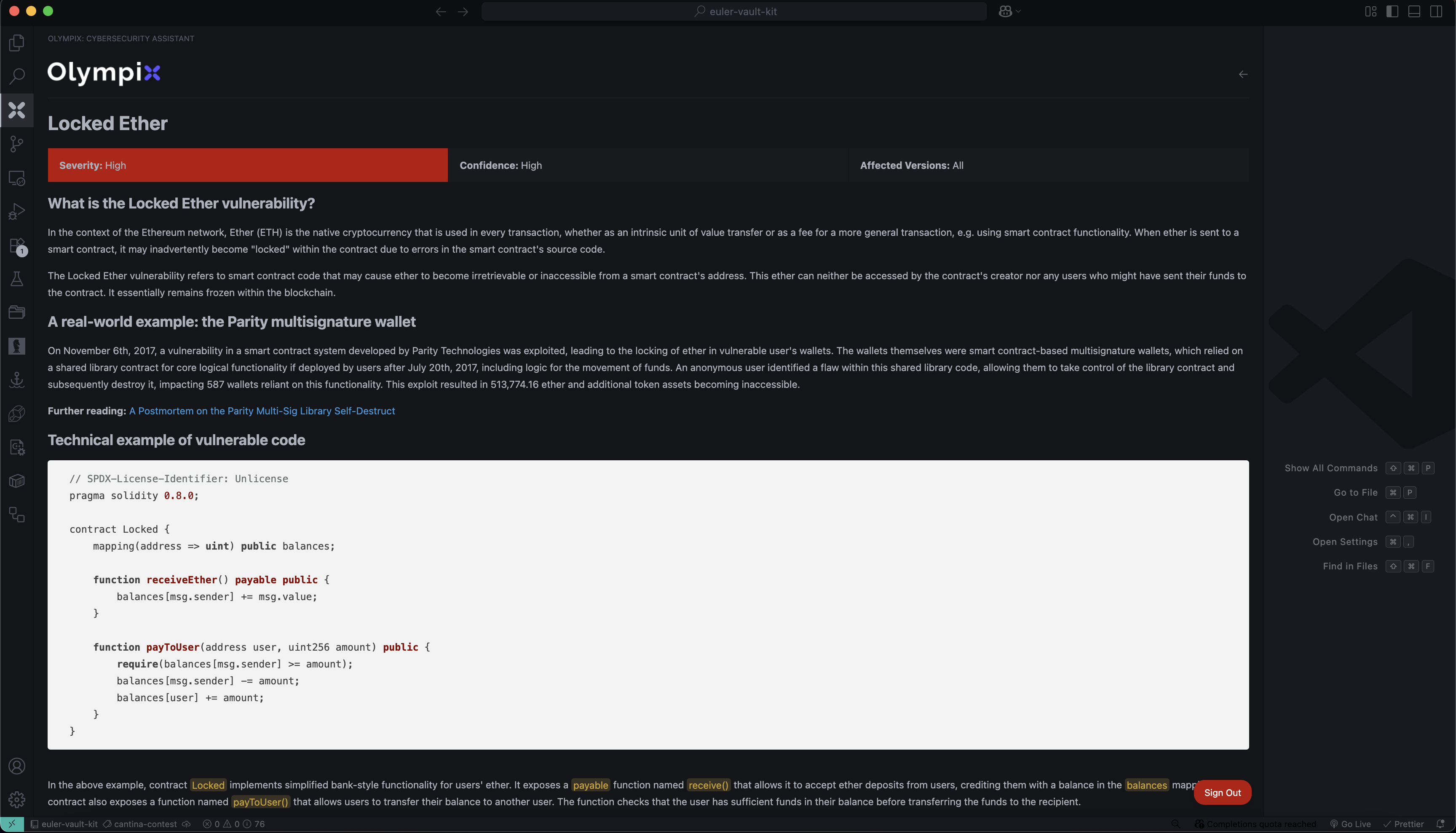
Vulnerable code:
Here, receiveEther lets users deposit ETH, and payToUser only updates an internal ledger—there is no withdraw function to send ETH out.
Fix: add a withdraw function
Vulnerability 2: abi.encodePacked with Dynamic Types
What is the issue?
abi.encodePacked(...) concatenates arguments tightly. If you pack multiple dynamic types, different inputs can collide, leading to the same hash.
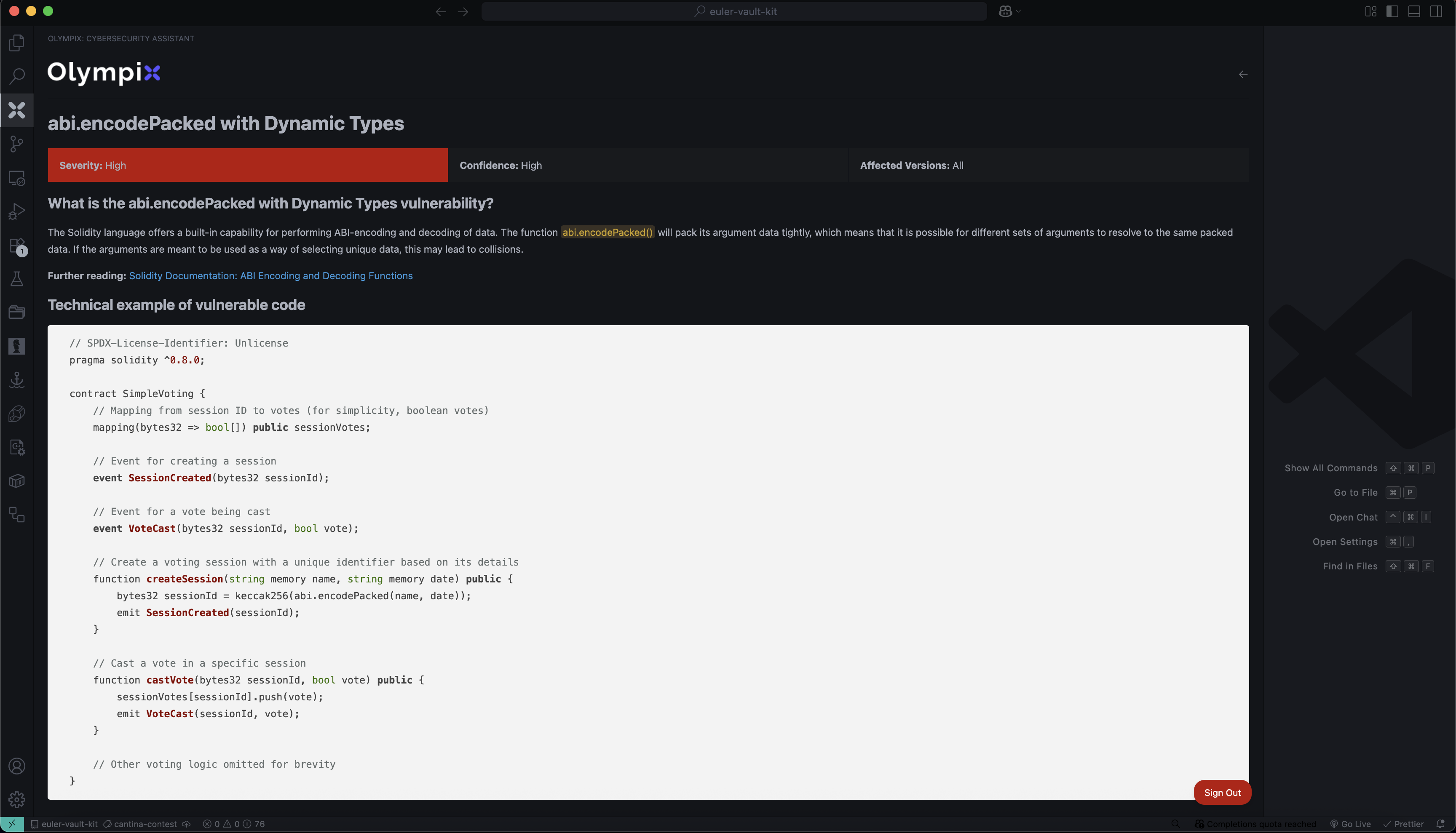
Vulnerable code:
Two different (name, date) pairs can produce the same sessionId.
Fix: use abi.encode or a single dynamic argument
Vulnerability 3: Unchecked Block with Subtraction
What is the issue?
Inside an unchecked { ... } block, arithmetic will wrap on underflow/overflow instead of reverting—potentially giving a malicious user an inflated balance.
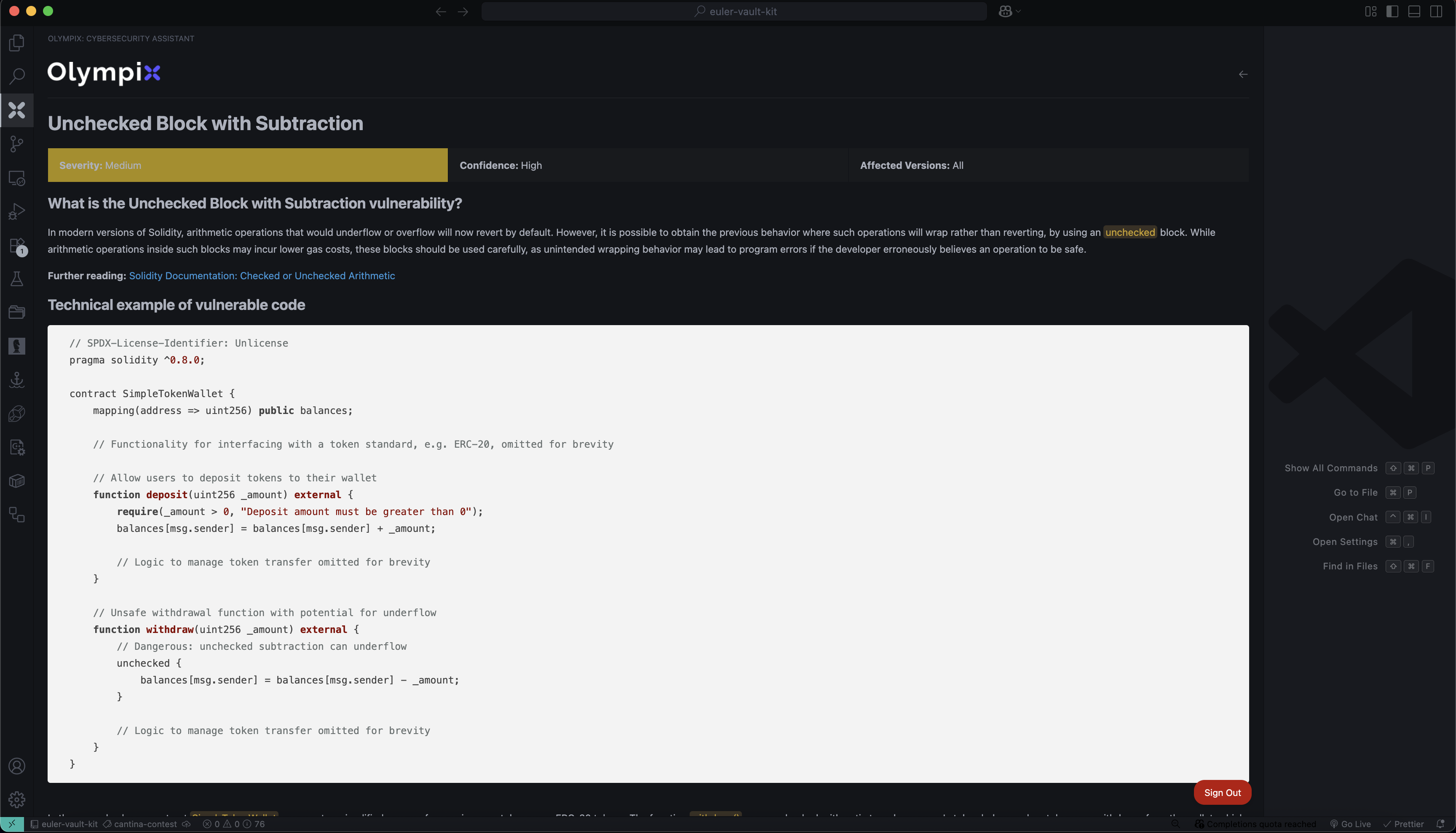
Vulnerable code:
If _amount exceeds the balance, balances[msg.sender] underflows to a huge value.
Fix: rely on Solidity >=0.8’s built-in checks (no unchecked), or validate manually:
These were a few examples showcasing the capabilities of Olympix AI, you can review the full report in the Olympix pane and click into any finding for detailed AI explanations, call stacks, and suggested fixes.
Conclusion
You’ve now seen how to use Olympix AI to scan any Solidity project for security issues. Integrating AI into your code review process can surface subtle bugs, speed up audits, and help teams ship more secure smart contracts from the get go.
You can also learn how to set up BuildBear CI/CD in a Foundry repository and run automation jobs by following this tutorial: BuildBear CI/CD Tutorial
Bonus: Olympix CI/CD & BuildBear Integration
Beyond interactive scanning, Olympix also offers a CI/CD GitHub Action for automated security analysis directly within your deployment pipelines. This allows teams to:
- Automatically scan every pull request or commit.
- Upload findings to GitHub Code Scanning or export JSON reports.
- Catch security regressions before merge.
To further enhance your pipeline:
- Combine Olympix CI/CD with BuildBear’s CI/CD platform.
- Olympix ensures your codebase is secure.
- BuildBear deploys your contracts in isolated sandboxes, executes tests, and verifies behavior post-deployment.
Using both together ensures that your code isn’t just safe at rest but also behaves securely in runtime.
Next Steps
What are Modular Smart Accounts in Web3
In the evolving world of Web3, developers are challenged to streamline blockchain transactions and make them user-friendly. Modular Smart Accounts play a crucial role in this journey by providing customization and flexibility. This article delves into the world of modular smart accounts, examining how platforms like Biconomy and Alchemy contribute to enhancing the Web3 user experience.
Execute Token Swaps on Uniswap V3 with Pimlico Alto & BuildBear
Pimlico Alto simplifies bundling user operations into transactions and submitting them to the blockchain via standard JSON-RPC requests.